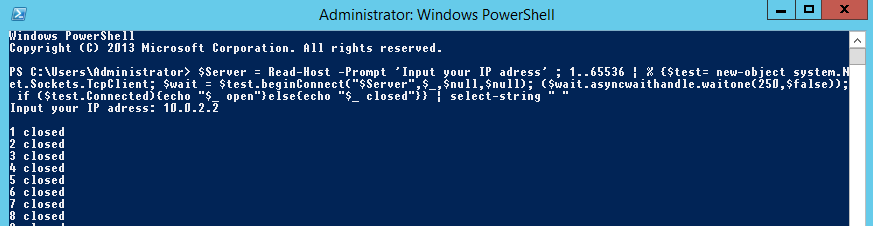
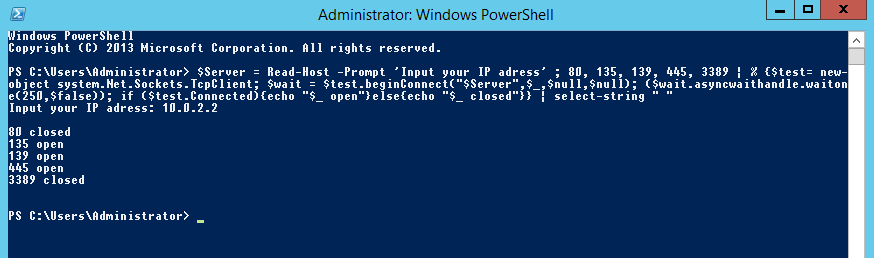
How to conduct a PowerShell Port Scan. Using PowerShell to conduct a simple port scan is very useful. If you have compromised a Windows server on a pentest and want to conduct a quick port scan you can use PowerShell. This might be to verify open ports on a neighboring system or to check egress filtering outbound to the internet using a public IP.
Using this simple one liner will produce a port scan of all ports 1-65536, the code snippet will also ask you for the IP address you want to port scan. Of course you can swap out the port range or simply substitute the ‘1..65536’ for something shorter like ’80, 445, 3389′ just like in the second example:
$Server = Read-Host -Prompt 'Input your target IP/host' ; 1..65536 | % {$test= new-object system.Net.Sockets.TcpClient; $wait = $test.beginConnect("$Server",$_,$null,$null); ($wait.asyncwaithandle.waitone(250,$false)); if ($test.Connected){echo "$_ open"}else{echo "$_ closed"}} | select-string " "
$Server = Read-Host -Prompt 'Input your target IP/host' ; 80, 445, 3389 | % {$test= new-object system.Net.Sockets.TcpClient; $wait = $test.beginConnect("$Server",$_,$null,$null); ($wait.asyncwaithandle.waitone(250,$false)); if ($test.Connected){echo "$_ open"}else{echo "$_ closed"}} | select-string " "
And in action this looks like the below: