Pwnkit, this is a bad one a really bad one as the “Policy Toolkit” “Polkit” package is installed by default on almost every major Linux operating system distribution after 2009.
Pwnkit was discoved by Qualys and reported 2021-11-18, they have a good technical write up located here: https://www.qualys.com/2022/01/25/cve-2021-4034/pwnkit.txt
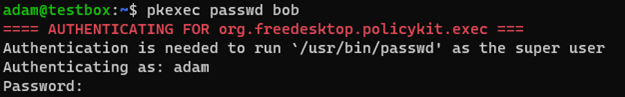
The Polkit package was first released in 2009 therefore the OS needs to be newer than this date, but not updated after January 2022. It essentially allows for an unprivileged user to interact with the pkexec utility to gain full local privilege escalation with relative ease. Polkit can be thought of as similar to sudo, pkexec is the front end SUID-root program, both in gui and cli form. pkexec takes a number of command line arguments like below:
The crux of the vulnerability lies within passing x amount of arguments to produce and out of bounds write, eventually overwriting a system environment variable.
Exploit:
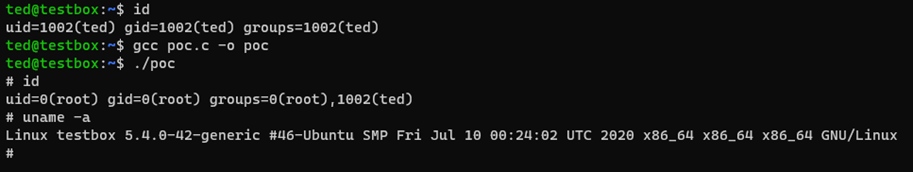
We will use the following exploit code by Andris Raugulis located here to gain LPE. We will simply compile with gcc and run as below:
As you can see this instantly pops root privs. For info this is a recent Ubuntu server.
Fix:
Patches are being rolled out however the recommended temporary fix by Qualys is to remove the SUID bit from the pkexec binary. This can be done with a command such as the following:
chmod 0755 /usr/bin/pkexec
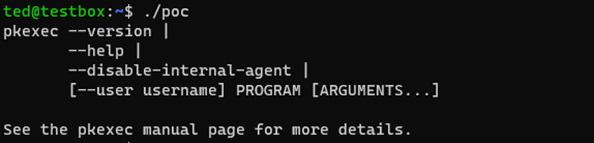
If you run the exploit against a patched system it simply return the pkexec help menu: