In this post I will walk through how to use MBSA – Microsoft Baseline Security Analyser. We can use MBSA to baseline our systems to ensure they are receiving the correct patches. This should be done regularly.
The classic screen that tells us Windows is up to date should not be relied upon.
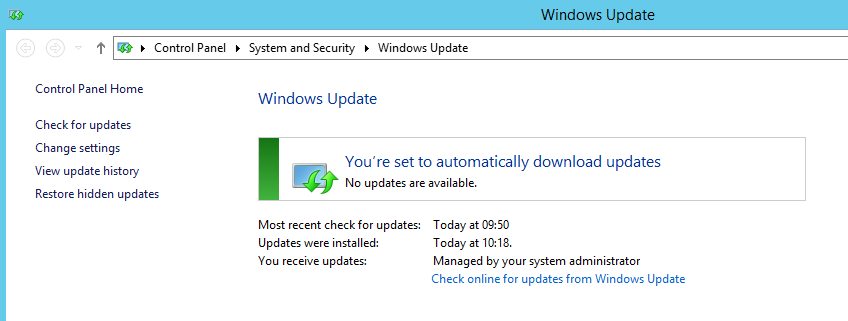
Most enterprise client machines will be checking into a WSUS or SCCM type update/package distributor. Its status will be based on what packages are available from the local server not Microsoft or a 3rd party entity. If WSUS is not configured correctly; for example, the correct product selection isn’t maintained there will be gaps. Or if your clients are not checking in properly. Worse your clients and servers are not being patched with the latest security updates! The above screen really isn’t good enough to know whether all updates are actually installed. MBSA can help you resolve issues like this by evaluating what patches are needed against Microsoft directly. ie the latest set of Microsoft updates.
So here is a quick run down on how to install MBSA and how to use it.
A quick search in Google for ‘MBSA’ will reveal the following page, follow the link and download your language.
On to the install – super easy next next next … etc.
The install couldn’t be easier.
This should leave you with a desktop icon, double click on this to launch MBSA. From here it is a simple case of selecting the right PC or Server that want to check. Remember for the machine you want to scan you will need administrative privileges.
To scan a machine, select ‘scan a computer’:
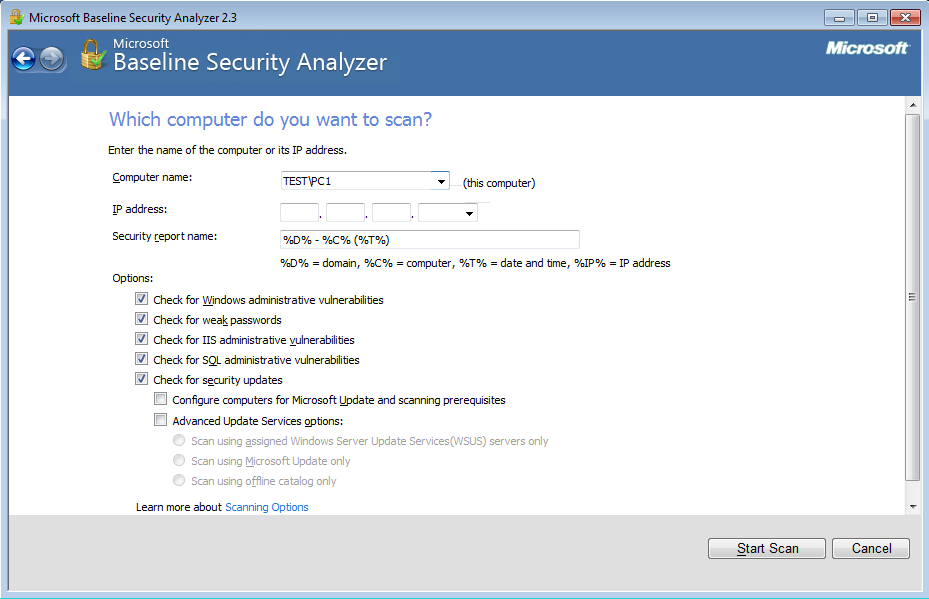
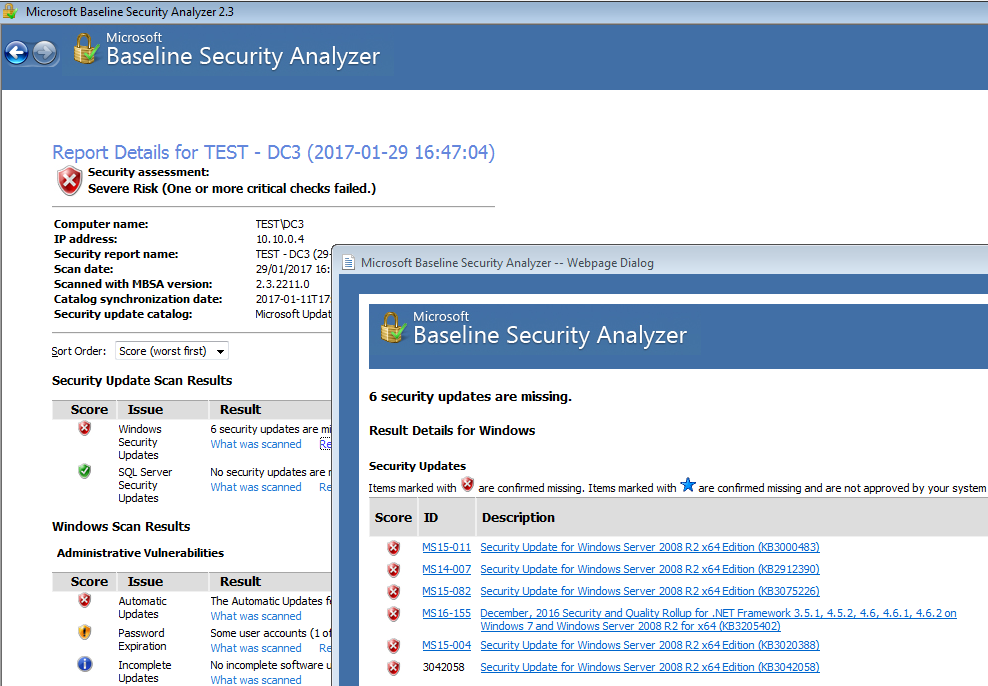
The results will then look something similar to the below (well hopefully not as this machine is out of date specifically to show you how it may look, hopefully yours is right up to date):
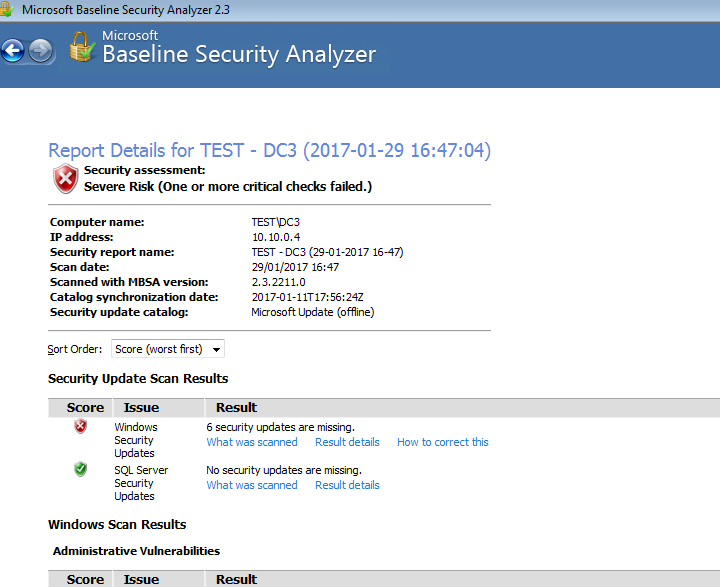
As you can see the there are 6 security updates missing, click on result details to see the missing patches:
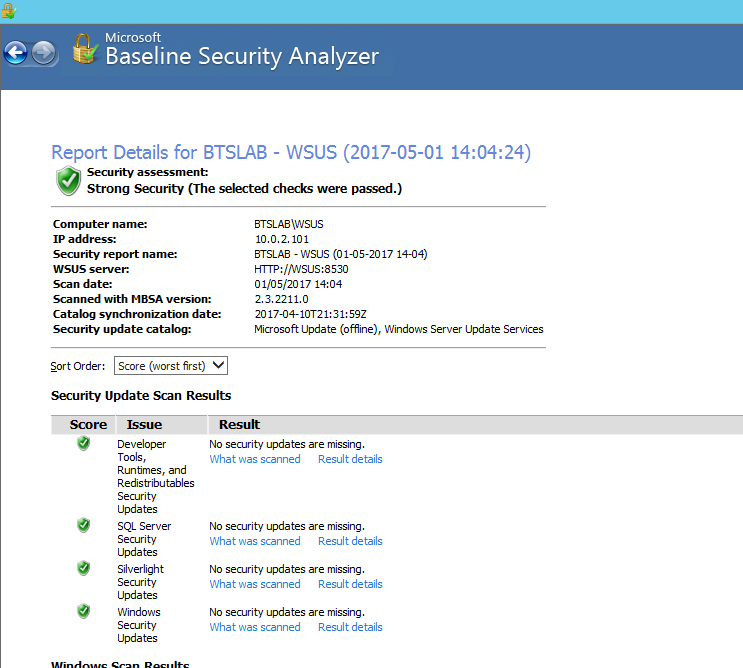
This is what it should look like with a clean bill of health:
From here you should investigate why the patches are missing if you are missing any. If you are using WSUS this could be due to the product selection or even classification not being correctly selected. You can check for these in your WSUS console. In Options – Products and Classifications – in a screen that looks like this:
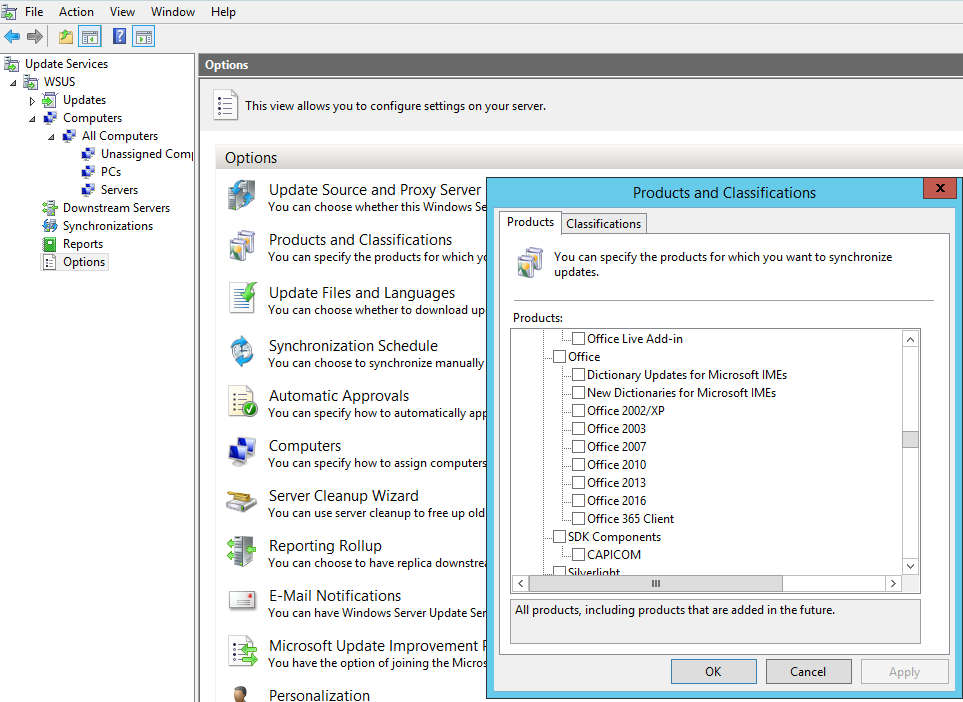
Note in this screen shot there is a selection for Office updates that you can apply. Don’t forget these type of applications in your selection, they are commonly missed!
Dig a bit deeper into your wsus and windows config to see whats going on. Ideally you should baseline your build images regularly to ensure they are getting the correct patches!
If you still find you are having issues with clients not being up to date check out the following script I posted about here. This can be run on a client or server machine, this helps clients check back into WSUS.