We can harden the Windows Client/Server Remote Desktop Protocol (RDP) in several ways using either local settings or preferable through Group Policy. As a minimum we should harden RDP in the following ways:
- Using Network Level Authentication (NLA).
- Setting Terminal Services Encryption Level to High.
- Force the use of TLS 1.0 protocol as a transport layer for the service.
- Setting the local security policy of the either the server or client to use only FIPS-140 compliant cryptography.
This post will we go through how we can accomplish these tasks.
Network Level Authentication (NLA)
Network level authentication allows the client to authenticate earlier in the remote connection process rather than the normal process. This option is most commonly seen in the Remote Desktop settings in the system properties as below:
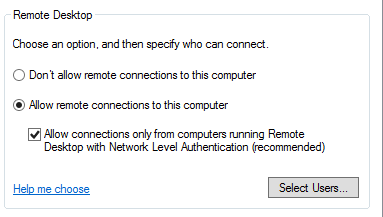
However it is far easier to set this via Group Policy and distribute to all your Servers as below:
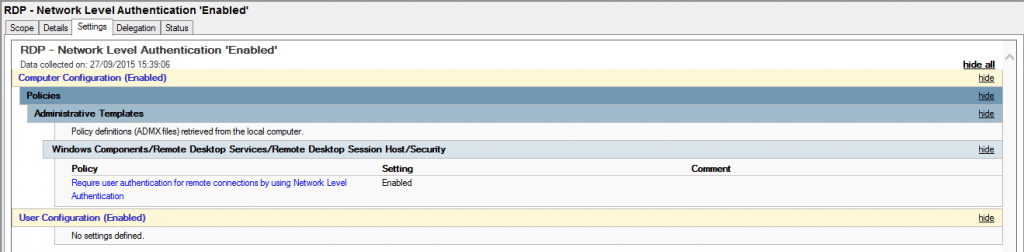
This can be applied to both Servers and workstations from Windows Vista and above.
Setting Terminal Services Encryption Level to High
Setting the Encryption level to High encrypts data sent from client to server and server to clients using 128 bit encryption. Like with the above example we can set the Terminal Services Encryption level to High either locally on the server or via Group Policy. In a domain environment the GPO is the way to go. With windows server 2008 this could be set locally through the GUI by navigating from the start menu–>Administrative Tools–>Remote Desktop Services–>Remote Desktop Session Host Configuration, then double clicking on the ‘RDP-TCP’ connection in the middle of the screen. The Encryption level can be found on the General tab as below:
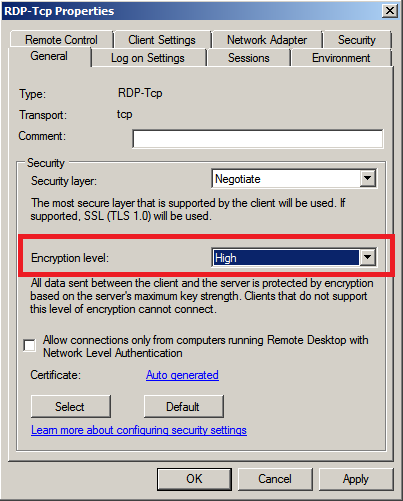
Unfortunately Microsoft removed the ‘RD Session Host Configuration’ options as standard with Server 2012 R2. Rather than adding in the whole RDS role to apply this option in the GUI you can apply it via GPO which will in turn apply to both 2008 and 2012 as below:
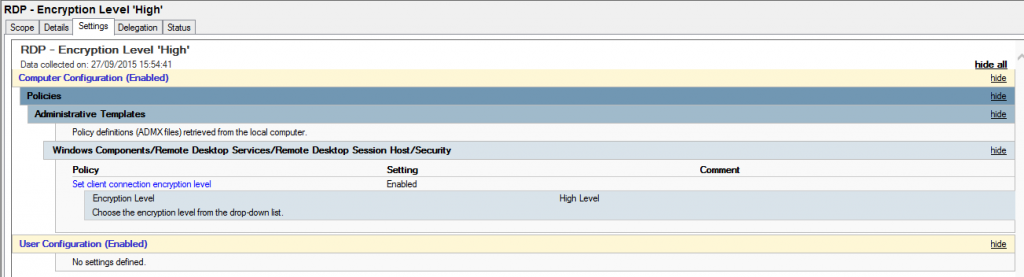
Force the use of TLS 1.0 protocol as a transport layer for the service
Forcing the use of TLS 1.0 mitigates the risks associated with SSL 3.0 protocol. Like with the previous option this can only be set in the GUI locally on Windows Server 2008. With this being said, and from a management perspective GPO is our preferred option, in order to apply this setting to both Windows Server 2008 and 2012.
This option is set in Windows Server 2008 locally by navigating from the start menu–>Administrative Tools–>Remote Desktop Services–>Remote Desktop Session Host Configuration, then double clicking on the ‘RDP-TCP’ connection in the middle of the screen as below:
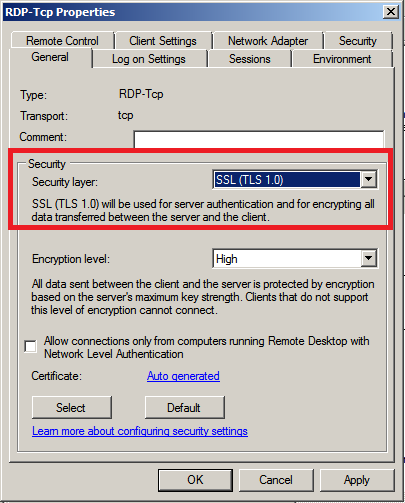
The GPO is located here:
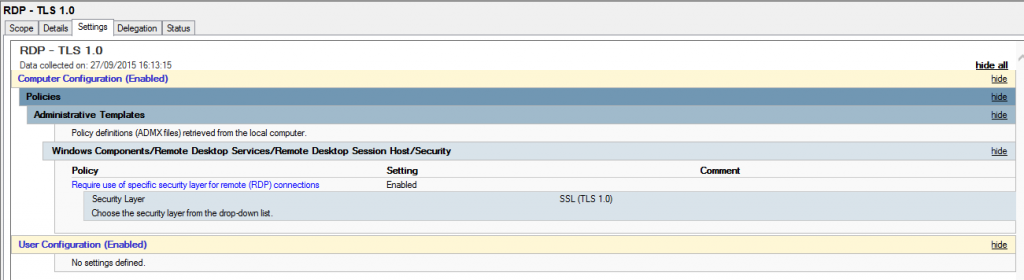
Setting the local security policy of the either the server or client to use only FIPS-140 compliant cryptography
This hardening technique can be accomplished by enabling the ‘System Cryptography’ through the Local computer policy editor or through GPO via the domain. It will force the use of FIPS-140 compliant cryptography for either the client or server across the system. This is windows system setting rather than an RDP setting, however by setting this you will be forcing the use of FIPS-140 compliant cryptography for Remote Desktop settings. If this setting is enabled only the FIPS-140 approved cryptographic algorithms are used: 3DES and AES for encryption, RSA or ECC public key for TLS key exchange and SHA256, SHA284 and SHA512 for TLS hashing. In the case of Remote Desktop it will only use 3DES.
Adding through the local computer policy can be achieved by opening a Microsoft Managment Console (MMC) adding a snap in; Group Policy Object Editor. As below:
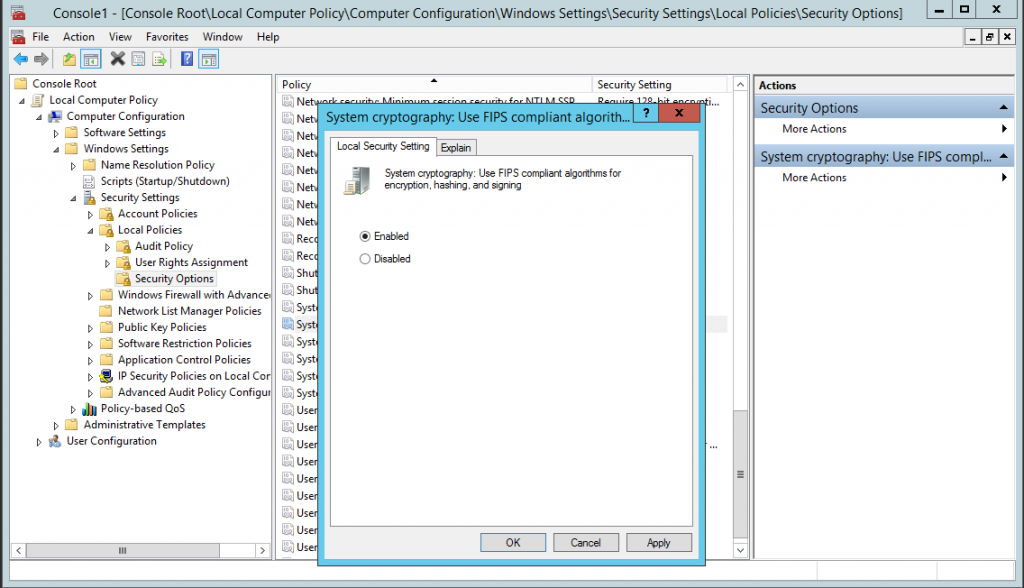
Setting via GPO can be achieved as below:
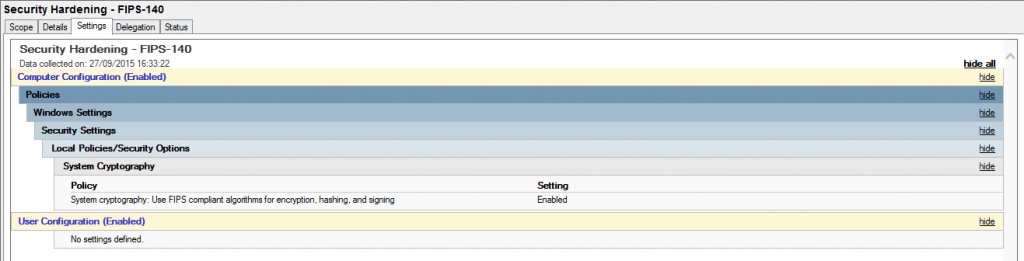
Hardening RDP – GPO Settings
Putting all these settings together in one GPO would look something like this:
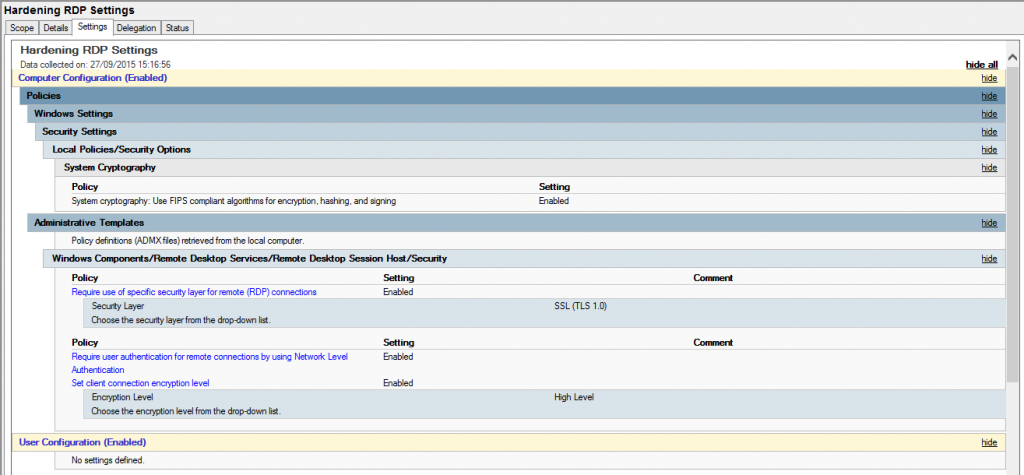
It clearly goes without saying you should first test these methods out for yourself in a safe test environment first before diving into your main production domain or web servers. Adding higher grade encryption to your communications across the domain may have extra computation costs in terms of performance on your network.
